IAM is not a new concept or solely a technology. Ad Master AWS concepts learn to design implement AWS solutions.

Gartner Recently Named Okta As A Leader In The 2017 Magic Quadrant For Access Management Management Leader Magic
It is vital to have accurate and timely information regarding the roles and relationships of all constituents of the.
. Identity Management Institute IMI is the leading global certification organization serving professionals in identity governance access management and data protection. Each time a user wanted to use a new web application they filled in a form to create an account. The history of identity and access management began as a security concept long before it became relevant to cybersecurity.
We have conducted research developed prototypes and reference implementations. Since 2007 IMI certifications help global members advance in their careers and gain the trust of the business communities they serve with their identity and access management. In past decades and centuries identity and access management would mean showing proof of identity through credentials to be able to enter a certain location or receive certain privileges.
In the past the standard for identity and access management was for a system to create and manage its own identity information for its users. Many companies limit access to physical offices by requiring security personnel to check employee ID badges or authorize guest access. IdM systems fall under the overarching umbrellas of IT security and data management.
Identity and access management is a comprehensive and unified approach to managing the identities of persons and processes issued by the University for the purpose of granting and controlling access to information resources. One of the earliest forms of digital identity management was ACLs or Access-Control Lists. Identity and access management IAM is a framework that allows the IT team to control access to systems networks and assets based on each users identity.
NIST has a rich history in digital identity standardization spanning more than 50 years. History of identity and access management. The use of cryptography to limit access to sensitive information dates back 3500 years to Mesopotamia when a craftsperson encrypted a valuable recipe for a pottery glaze.
Titles such as king countess bishop. Ad Browse Discover Thousands of Computers Internet Book Titles for Less. IAM is comprised of the systems and processes that allow IT administrators to assign a single digital identity to each entity authenticate them when they log in authorize them to access specified resources and monitor and manage those identities throughout their lifecycle.
People services and servers automate access controls and meet compliance requirements across traditional and containerized environments. Access Management In the past access management was achieved through encryption to make sure vulnerable data didnt land in the wrong hands. Identity and access management IAM is a centralized and consistent way to manage user identities ie.
The concept of identity existed long before the invention of the computer and the need for. The primary benefit for these end users is that processes are streamlined and smooth. With IAM employees use a predetermined identity to gain secure access to the IT resources they need to do their job.
Digital identity for access control is a fundamental and critical cybersecurity capability that ensures the right people and things have the right access to the right resources at the right time. Identity management also known as identity and access management is a framework of policies and technologies to ensure that the right users have the appropriate access to technology resources. Identity access management represents the perfect marriage of productivity security and access to best-in-class tools.
A Brief History of Identity Management The Importance of Identity. Verifies the identity of the user based on existing information in an identity management database. Start your free trial.
From beginner to guru we can help you get hands-on training with AWS cloud technologies. IAM consists of two main components. One example of an IAM solution in action is when employees use a VPN to access company resources for remote.
Identity and access management systems not only identify authenticate. Stated differently identity management handled getting you your ticket to the party access management handled verifying that ticket once you got to the party and what that ticket allowed you to do. James Brewer Director of IAM Office of Information Security OIS will present a first-person history of the evolution of Identity and Access Management software from the late 1990s to today covering the emergence of web applications how cookies made web SSO work what Federation and SAML mean what LDAP directories are what meta-directories were and.
IAM is not just for employees anymore.

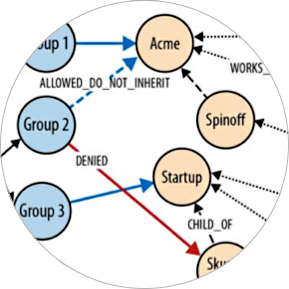
Graph Databases For Identity Access Management Uses Cases

Identity Attack Vectors Implementing An Effective Identity And Access Management Solution Paperback Walmart Com Management Solutions Identity

Blockchain For Digital Identity The Decentralized And Self Sovereign Identity Ssi 101blockchains Via Mike Blockchain Identity Digital Transformation

What Is Identity And Access Management Iam Sso Mfa And Idaas Definitions Ibm


0 comments
Post a Comment